505 lines
32 KiB
Markdown
505 lines
32 KiB
Markdown

|
||
|
||
```
|
||
root@pc1:~# tcpdump -i eth1
|
||
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
|
||
listening on eth1, link-type EN10MB (Ethernet), snapshot length 262144 bytes
|
||
19:35:04.553056 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo request, id 38058, seq 1, length 64
|
||
19:35:04.555038 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo reply, id 38058, seq 1, length 64
|
||
19:35:05.554500 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo request, id 38058, seq 2, length 64
|
||
19:35:05.555265 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo reply, id 38058, seq 2, length 64
|
||
19:35:06.555772 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo request, id 38058, seq 3, length 64
|
||
19:35:06.556673 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo reply, id 38058, seq 3, length 64
|
||
19:35:07.557110 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo request, id 38058, seq 4, length 64
|
||
19:35:07.557961 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo reply, id 38058, seq 4, length 64
|
||
19:35:08.558528 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo request, id 38058, seq 5, length 64
|
||
19:35:08.559256 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo reply, id 38058, seq 5, length 64
|
||
19:35:08.722292 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo request, id 10952, seq 1, length 64
|
||
19:35:08.722331 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo reply, id 10952, seq 1, length 64
|
||
19:35:09.631016 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, neighbor solicitation, who has fe80::216:3eff:fe00:2, length 32
|
||
19:35:09.631064 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, neighbor advertisement, tgt is fe80::216:3eff:fe00:2, length 24
|
||
19:35:09.723566 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo request, id 10952, seq 2, length 64
|
||
19:35:09.723596 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo reply, id 10952, seq 2, length 64
|
||
19:35:10.724802 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo request, id 10952, seq 3, length 64
|
||
19:35:10.724838 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo reply, id 10952, seq 3, length 64
|
||
19:35:11.726031 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo request, id 10952, seq 4, length 64
|
||
19:35:11.726064 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo reply, id 10952, seq 4, length 64
|
||
19:35:12.727250 IP6 fe80::216:3eff:fe00:4 > fe80::216:3eff:fe00:2: ICMP6, echo request, id 10952, seq 5, length 64
|
||
19:35:12.727282 IP6 fe80::216:3eff:fe00:2 > fe80::216:3eff:fe00:4: ICMP6, echo reply, id 10952, seq 5, length 64
|
||
```
|
||
|
||
|
||
|
||
```
|
||
root@pc1:~# python3 208.py
|
||
Ether / fe80::216:3eff:fe00:2 > ff02::16 (0) / IPv6ExtHdrHopByHop / ICMPv6MLReport2
|
||
Ether / fe80::216:3eff:fe00:2 > ff02::16 (0) / IPv6ExtHdrHopByHop / ICMPv6MLReport2
|
||
Ether / fe80::216:3eff:fe00:4 > ff02::16 (0) / IPv6ExtHdrHopByHop / ICMPv6MLReport2
|
||
Ether / fe80::216:3eff:fe00:4 > ff02::16 (0) / IPv6ExtHdrHopByHop / ICMPv6MLReport2
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x3d3d seq: 0x1)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x3d3d seq: 0x1)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x3d3d seq: 0x2)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x3d3d seq: 0x2)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x3d3d seq: 0x3)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x3d3d seq: 0x3)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x3d3d seq: 0x4)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x3d3d seq: 0x4)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x3d3d seq: 0x5)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x3d3d seq: 0x5)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x6b18 seq: 0x1)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x6b18 seq: 0x1)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x6b18 seq: 0x2)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x6b18 seq: 0x2)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x6b18 seq: 0x3)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x6b18 seq: 0x3)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x6b18 seq: 0x4) Ether / IPv6 / ICMPv6 Echo Reply (id: 0x6b18 seq: 0x4)
|
||
Ether / IPv6 / ICMPv6 Echo Request (id: 0x6b18 seq: 0x5)
|
||
Ether / IPv6 / ICMPv6 Echo Reply (id: 0x6b18 seq: 0x5)
|
||
```
|
||
|
||
|
||
|
||

|
||
|
||

|
||
|
||

|
||
|
||
```
|
||
buf :255 255 255 255 255 255 174 171 50 9 142 180 8 6 0 1 8 0 6 4 0 1 174 171 50 9 142 180 10 5 1 1 0 0 0 0 0 0 10 5 1 2 0 0 0 0 0 0 0 0 0 0 0 22 58 0 5 2 0 0 1 0 143 0 117 226 0 0 0 1 4 0 0 0 255 2 0 0 0 0 0 0 0 0 0 1 255 9 142 180 0 0 0 0 0 0 0 0 0 0 0 0 0 0 156 111 139 231 79 127 0 0 95 154 127 103 0 0 0 0 1 0 0 0 0 0 0 0 228 77 109 231 79 127 0 0 240 212 138 231 79 127 0 0 9 0 0 0 0 0 0 0 164 115 139 231 79 127 0 0 196 0 0 0 0 0 0 0 16 78 110 231 79 127 0 0 0 112 138 231 79 127 0 0 216 182 6 248 254 127 0 0 212 182 6 248 254 127 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 16 78 110 231 79 127 0 0 224 111 109 231 79 127 0 0 49 217 138 231 79 127 0 0 95 154 127 103 0 0 0 0 105 254 157 1 0 0 0 0 212 182 6 248 254 127 0 0 32 117 138 231 79 127 0 0 160 183 6 248 254 127 0 0 240 212 138 231 79 127 0 0 144 183 6 248 254 127 0 0 3 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 95 154 127 103 0 0 0 0 232 148 141 231 79 127 0 0 49 217 138 231 79 127 0 0 184 184 6 248 254 127 0 0 144 183 6 248 254 127 0 0 160 183 6 248 254 127 0 0 225 124 139 231 79 127 0 0 1 0 0 0 0 0 0 0 168 121 138 231 79 127 0 0 9 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 232 137 141 231 79 127 0 0 48 151 141 231 79 127 0 0 168 121 138 231 79 127 0 0 232 137 141 231 79 127 0 0 0 0 0 0 1 0 0 0 232 148 141 231 79 127 0 0 0 0 0 0 0 0 0 0 216 210 10 248 254 127 0 0 184 209 10 248 254 127 0 0 255 255 255 255 0 0 0 0 83 143 48 104 0 0 0 0 64 130 109 231 79 127 0 0 0 112 138 231 79 127 0 0 88 151 141 231 79 127 0 0 176 184 6 248 254 127 0 0 192 185 6 248 254 127 0 0 3 0 0 0 0 0 0 0 208 184 6 248 254 127 0 0 100 223 139 231 79 127 0 0 217 118 141 231 79 127 0 0 80 223 138 231 79 127 0 0 48 185 6 248 254 127 0 0 7 0 0 0 0 0 0 0 7 0 0 0 8 0 0 0 240 212 138 231 79 127 0 0 232 137 141 231 79 127 0 0 77 146 139 231 79 127 0 0 0 0 0 0 0 0 0 0 216 160 139 231 79 127 0 0 128 184 6 248 254 127 0 0 200 197 110 231 79 127 0 0 8 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 185 6 248 254 127 0 0 0 0 0 0 0 0 0 0 0 185 6 248 254 127 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 96 215 138 231 79 127 0 0 232 148 141 231 79 127 0 0 132 217 138 231 79 127 0 0 48 212 138 231 79 127 0 0 72 128 141 231 79 127 0 0 0 208 138 231 79 127 0 0 0 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 64 130 109 231 79 127 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 186 183 144 108 127 166 0 0 3 232 138 108 127 166 0 0 128 145 141 231 79 127 0 0 128 145 141 231 79 127 0 0 232 70 140 231 79 127 0 0 208 187 6 248 254 127 0 0 31 27 139 231 79 127 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 64 133 138 231 79 127 0 0 128 144 141 231 79 127 0 0 0 0 0 0 0 0 0 0 1 189 6 248 254 127 0 0 1 151 141 231 79 127 0 0 232 137 141 231 79 127 0 0 184 185 6 248 254 127 0 0 3 232 138 108 127 166 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 24 210 10 248 254 127 0 0 0 0 0 0 32 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 246 117 174 3 1 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 230 207 6 248 254 127 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 194 0 0 0 0 0 0 0 215 187 6 248 254 127 0 0 149 84 245 242 222 85 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0
|
||
Read 42 bytes from device tap0
|
||
```
|
||
|
||
```
|
||
buf :FF FF FF FF FF FF AE AB 32 09 8E B4 08 06 00 01 08 00 06 04 00 01 AE AB 32 09 8E B4 0A 05 01 01 00 00 00 00 00 00 0A 05 01 02 00 00 00 00 00 00 00 00 00 00 00 16 3A 00 05 02 00 00 01 00 8F 00 75 E2 00 00 00 01 04 00 00 00 FF 02 00 00 00 00 00 00 00 00 00 01 FF 09 8E B4 00 00 00 00 00 00 00 00 00 00 00 00 00 00 9C CF 46 E5 67 7F 00 00 5F 9A 7F 67 00 00 00 00 01 00 00 00 00 00 00 00 E4 AD 28 E5 67 7F 00 00 F0 34 46 E5 67 7F 00 00 09 00 00 00 00 00 00 00 A4 D3 46 E5 67 7F 00 00 C4 00 00 00 00 00 00 00 10 AE 29 E5 67 7F 00 00 00 D0 45 E5 67 7F 00 00 88 E3 64 9A FE 7F 00 00 84 E3 64 9A FE 7F 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 10 AE 29 E5 67 7F 00 00 E0 CF 28 E5 67 7F 00 00 31 39 46 E5 67 7F 00 00 5F 9A 7F 67 00 00 00 00 69 FE 9D 01 00 00 00 00 84 E3 64 9A FE 7F 00 00 20 D5 45 E5 67 7F 00 00 50 E4 64 9A FE 7F 00 00 F0 34 46 E5 67 7F 00 00 40 E4 64 9A FE 7F 00 00 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 5F 9A 7F 67 00 00 00 00 E8 F4 48 E5 67 7F 00 00 31 39 46 E5 67 7F 00 00 68 E5 64 9A FE 7F 00 00 40 E4 64 9A FE 7F 00 00 50 E4 64 9A FE 7F 00 00 E1 DC 46 E5 67 7F 00 00 01 00 00 00 00 00 00 00 A8 D9 45 E5 67 7F 00 00 09 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 E8 E9 48 E5 67 7F 00 00 30 F7 48 E5 67 7F 00 00 A8 D9 45 E5 67 7F 00 00 E8 E9 48 E5 67 7F 00 00 00 00 00 00 01 00 00 00 E8 F4 48 E5 67 7F 00 00 00 00 00 00 00 00 00 00 D8 52 6F 9A FE 7F 00 00 B8 51 6F 9A FE 7F 00 00 FF FF FF FF 00 00 00 00 53 8F 30 68 00 00 00 00 40 E2 28 E5 67 7F 00 00 00 D0 45 E5 67 7F 00 00 58 F7 48 E5 67 7F 00 00 60 E5 64 9A FE 7F 00 00 70 E6 64 9A FE 7F 00 00 03 00 00 00 00 00 00 00 80 E5 64 9A FE 7F 00 00 64 3F 47 E5 67 7F 00 00 D9 D6 48 E5 67 7F 00 00 50 3F 46 E5 67 7F 00 00 E0 E5 64 9A FE 7F 00 00 07 00 00 00 00 00 00 00 07 00 00 00 08 00 00 00 F0 34 46 E5 67 7F 00 00 E8 E9 48 E5 67 7F 00 00 4D F2 46 E5 67 7F 00 00 00 00 00 00 00 00 00 00 D8 00 47 E5 67 7F 00 00 30 E5 64 9A FE 7F 00 00 C8 25 2A E5 67 7F 00 00 08 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 B0 E5 64 9A FE 7F 00 00 00 00 00 00 00 00 00 00 B0 E5 64 9A FE 7F 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 60 37 46 E5 67 7F 00 00 E8 F4 48 E5 67 7F 00 00 84 39 46 E5 67 7F 00 00 30 34 46 E5 67 7F 00 00 48 E0 48 E5 67 7F 00 00 00 30 46 E5 67 7F 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 40 E2 28 E5 67 7F 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 01 33 C8 BC BE A7 00 00 3F 90 B0 BC BE A7 00 00 80 F1 48 E5 67 7F 00 00 80 F1 48 E5 67 7F 00 00 E8 A6 47 E5 67 7F 00 00 80 E8 64 9A FE 7F 00 00 1F 7B 46 E5 67 7F 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 40 E5 45 E5 67 7F 00 00 80 F0 48 E5 67 7F 00 00 00 00 00 00 00 00 00 00 01 EA 64 9A FE 7F 00 00 01 F7 48 E5 67 7F 00 00 E8 E9 48 E5 67 7F 00 00 68 E6 64 9A FE 7F 00 00 3F 90 B0 BC BE A7 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 18 52 6F 9A FE 7F 00 00 00 00 00 00 20 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 F6 75 AE 03 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 E6 EF 64 9A FE 7F 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 C2 00 00 00 00 00 00 00 87 E8 64 9A FE 7F 00 00 F5 64 7B 22 E1 55 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|
||
Read 42 bytes from device tap0
|
||
```
|
||
|
||
```
|
||
buf :FF FF FF FF FF FF AE AB 32 09 8E B4 08 06 00 01 08 00 06 04 00 01 AE AB 32 09 8E B4 0A 05 01 01 00 00 00 00 00 00 0A 05 01 02
|
||
Read 42 bytes from device tap0
|
||
```
|
||
|
||
```
|
||
buf :FF FF FF FF FF FF AE AB 32 09 8E B4 08 06 00 01 08 00 06 04 00 01 AE AB 32 09 8E B4 0A 05 01 01 00 00 00 00 00 00 0A 05 01 03
|
||
Read 42 bytes from device tap0
|
||
```
|
||
|
||
|
||
|
||
00:16:3e:00:00:04
|
||
|
||
52:5e:a1:8f:e3:6a
|
||
|
||
|
||
|
||
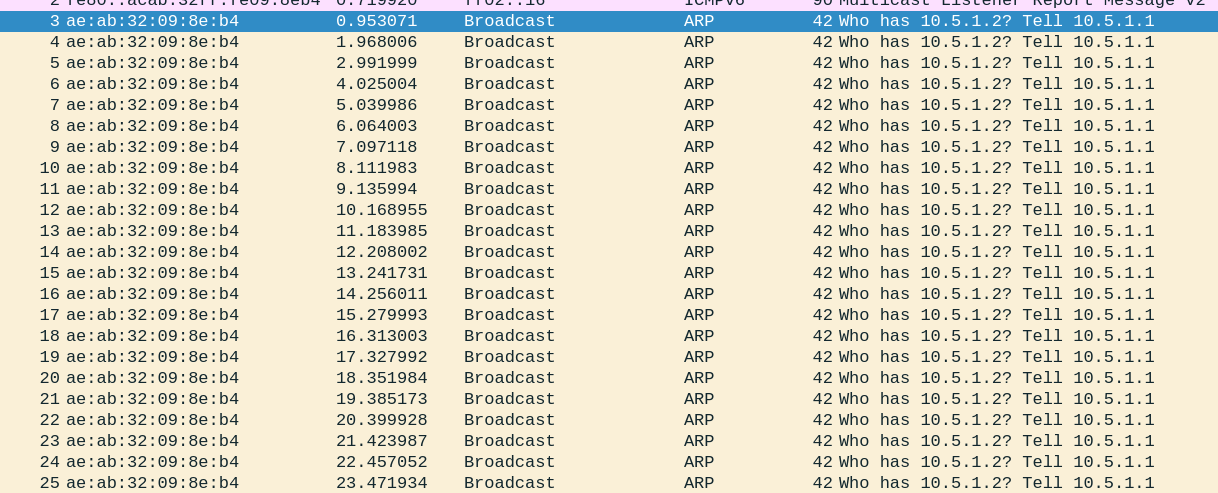
根据提供的 `buf` 内容,可以解析出这是一个 **ARP 请求包**。以下是详细的解析步骤。
|
||
|
||
---
|
||
|
||
### **1. ARP 数据包结构**
|
||
|
||
ARP 请求包的基本结构如下:
|
||
|
||
| 字段名称 | 长度(字节) | 说明 |
|
||
| --------------------- | ------------ | ---------------------------------------------- |
|
||
| 目标 MAC 地址 | 6 | 广播地址(`FF:FF:FF:FF:FF:FF`) |
|
||
| 源 MAC 地址 | 6 | 发送方的 MAC 地址 |
|
||
| 上层协议类型 | 2 | 表示这是一个 ARP 包(值为 `0x0806`) |
|
||
| 硬件类型 | 2 | 通常为以太网(值为 `0x0001`) |
|
||
| 协议类型 | 2 | 表示 IP 协议(值为 `0x0800`) |
|
||
| 硬件地址长度 | 1 | MAC 地址的长度,通常为 6 |
|
||
| 协议地址长度 | 1 | IP 地址的长度,通常为 4 |
|
||
| 操作码 | 2 | `0x0001` 表示 ARP 请求,`0x0002` 表示 ARP 响应 |
|
||
| 发送方硬件地址(SHA) | HLEN(6) | 发送方的 MAC 地址 |
|
||
| 发送方协议地址(SPA) | PLEN(4) | 发送方的 IP 地址 |
|
||
| 目标硬件地址(THA) | HLEN(6) | 目标的 MAC 地址,ARP 请求中为全 0 |
|
||
| 目标协议地址(TPA) | PLEN(4) | 目标的 IP 地址 |
|
||
|
||
---
|
||
|
||
### **2. 提供的 `buf` 内容**
|
||
原始数据:
|
||
```
|
||
FF FF FF FF FF FF AE AB 32 09 8E B4 08 06 00 01 08 00 06 04 00 01 AE AB 32 09 8E B4 0A 05 01 01 00 00 00 00 00 00 0A 05 01 02
|
||
```
|
||
|
||
**分解字段:**
|
||
| 偏移 | 字节范围 | 内容 | 解析说明 |
|
||
| ---- | ------------------- | ------------------------------------------ | -------------------------------------------- |
|
||
| 0 | `FF FF FF FF FF FF` | 目标 MAC 地址:广播地址 | 目标为全网广播 |
|
||
| 6 | `AE AB 32 09 8E B4` | 源 MAC 地址:`AE:AB:32:09:8E:B4` | PC2 的 `tap0` MAC 地址 |
|
||
| 12 | `08 06` | 上层协议类型:ARP 包 (`0x0806`) | 表示这是一个 ARP 包 |
|
||
| 14 | `00 01` | 硬件类型:以太网 (`0x0001`) | 表示硬件类型为以太网 |
|
||
| 16 | `08 00` | 协议类型:IPv4 (`0x0800`) | 表示要解析的协议为 IPv4 |
|
||
| 18 | `06` | 硬件地址长度(HLEN):6 | MAC 地址长度为 6 字节 |
|
||
| 19 | `04` | 协议地址长度(PLEN):4 | IP 地址长度为 4 字节 |
|
||
| 20 | `00 01` | 操作码(OPER):请求 (`0x0001`) | 表示这是一个 ARP 请求包 |
|
||
| 22 | `AE AB 32 09 8E B4` | 发送方硬件地址(SHA):`AE:AB:32:09:8E:B4` | 发送方 MAC 地址,来自 PC2 的 `tap0` 接口 |
|
||
| 28 | `0A 05 01 01` | 发送方协议地址(SPA):`10.5.1.1` | 发送方 IP 地址 |
|
||
| 32 | `00 00 00 00 00 00` | 目标硬件地址(THA):`00:00:00:00:00:00` | 目标 MAC 地址为空,全零(未解析) |
|
||
| 38 | `0A 05 01 02` | 目标协议地址(TPA):`10.5.1.2` | 目标 IP 地址(PC1 的 `tap0` 接口的 IP 地址) |
|
||
|
||
---
|
||
|
||
### **3. 分析说明**
|
||
- **目标 MAC 地址(广播)**:
|
||
目标 MAC 地址是 `FF:FF:FF:FF:FF:FF`,表示这是一个广播包,发往子网内的所有设备。
|
||
|
||
- **源 MAC 地址**:
|
||
源 MAC 地址是 `AE:AB:32:09:8E:B4`,这对应 PC2 的 `tap0` 接口。
|
||
|
||
- **操作类型(请求)**:
|
||
操作码是 `0x0001`,表明这是一个 ARP 请求包。
|
||
|
||
- **发送方 IP 地址和 MAC 地址**:
|
||
发送方 IP 地址是 `10.5.1.1`,MAC 地址是 `AE:AB:32:09:8E:B4`。
|
||
|
||
- **目标 IP 地址**:
|
||
目标 IP 地址是 `10.5.1.2`,这对应 PC1 的 `tap0` 接口的 IP 地址。
|
||
|
||
- **目标 MAC 地址为空**:
|
||
因为这是一个 ARP 请求,目标的 MAC 地址尚未解析,所以此字段为全零。
|
||
|
||
---
|
||
|
||
### **4. 整体解析结果**
|
||
PC1 的 `tap0` 接口收到的 `buf` 是一个 **ARP 请求包**,由 PC2 的 `tap0` 接口发送,目的是解析目标 IP 地址 `10.5.1.2` 对应的 MAC 地址。
|
||
|
||
**PC1 的响应:**
|
||
- PC1 的 `tap0` 应该生成一个 ARP 响应包,包含以下信息:
|
||
- 目标 MAC 地址:`AE:AB:32:09:8E:B4`(PC2 的 MAC 地址)。
|
||
- 目标 IP 地址:`10.5.1.1`(PC2 的 IP 地址)。
|
||
- 源 MAC 地址:PC1 的 `tap0` 的 MAC 地址。
|
||
- 源 IP 地址:`10.5.1.2`(PC1 的 IP 地址)。
|
||
|
||
---
|
||
|
||
### **抓包工具验证**
|
||
你可以使用 `tcpdump` 或 `Wireshark` 来验证 ARP 包的内容:
|
||
```bash
|
||
sudo tcpdump -i tap0 -vv arp
|
||
```
|
||
或者在 Wireshark 中直接查看 ARP 请求的详细信息,与上述解析进行对比。
|
||
|
||
|
||
|
||
|
||
```
|
||
buf :FF FF FF FF FF FF AE AB 32 09 8E B4 08 06 00 01 08 00 06 04 00 01 AE AB 32 09 8E B4 0A 05 01 01 00 00 00 00 00 00 0A 05 01 02 00 00 00 00 00 00 00 00 00 00 00 00
|
||
|
||
```
|
||
=======
|
||
|
||
|
||
|
||
|
||
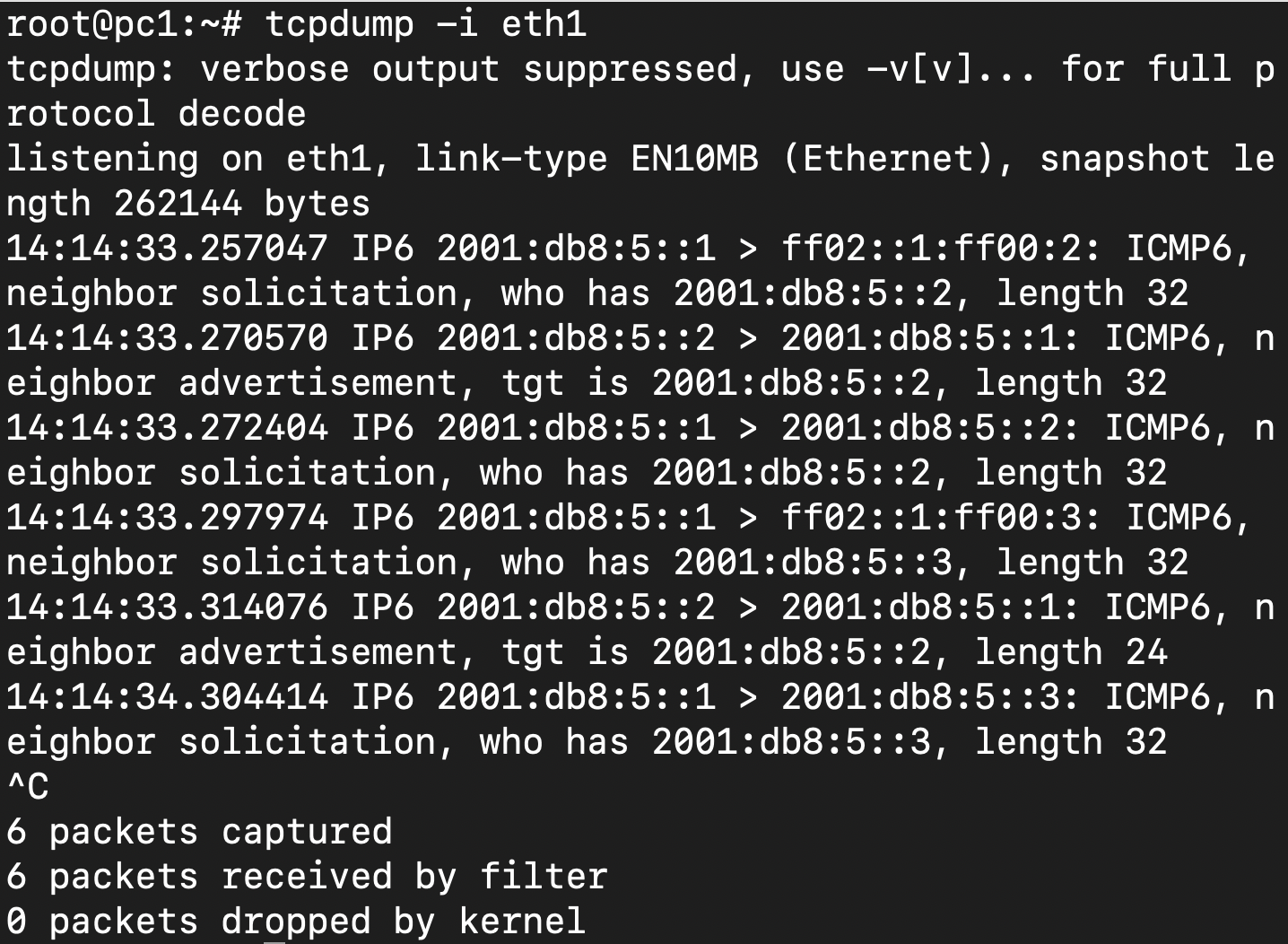
root@pc1:~# tcpdump -i eth1
|
||
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
|
||
listening on eth1, link-type EN10MB (Ethernet), snapshot length 262144 bytes
|
||
10:53:47.911087 IP6 2001:db8:5::2 > ff02::1:ff00:1: ICMP6, neighbor solicitation, who has 2001:db8:5::1, length 32
|
||
10:53:47.911189 IP6 2001:db8:5::1 > 2001:db8:5::2: ICMP6, neighbor advertisement, tgt is 2001:db8:5::1, length 32
|
||
10:53:47.912325 IP6 2001:db8:5::2 > 2001:db8:5::1: ICMP6, echo request, id 56760, seq 1, length 64
|
||
10:53:47.912349 IP6 2001:db8:5::1 > 2001:db8:5::2: ICMP6, echo reply, id 56760, seq 1, length 64
|
||
10:53:48.904692 IP6 2001:db8:5::2 > 2001:db8:5::1: ICMP6, echo request, id 56760, seq 2, length 64
|
||
10:53:48.904719 IP6 2001:db8:5::1 > 2001:db8:5::2: ICMP6, echo reply, id 56760, seq 2, length 64
|
||
10:53:49.906078 IP6 2001:db8:5::2 > 2001:db8:5::1: ICMP6, echo request, id 56760, seq 3, length 64
|
||
10:53:49.906103 IP6 2001:db8:5::1 > 2001:db8:5::2: ICMP6, echo reply, id 56760, seq 3, length 64
|
||
10:53:50.907512 IP6 2001:db8:5::2 > 2001:db8:5::1: ICMP6, echo request, id 56760, seq 4, length 64
|
||
10:53:50.907538 IP6 2001:db8:5::1 > 2001:db8:5::2: ICMP6, echo reply, id 56760, seq 4, length 64
|
||
10:53:51.908904 IP6 2001:db8:5::2 > 2001:db8:5::1: ICMP6, echo request, id 56760, seq 5, length 64
|
||
10:53:51.908929 IP6 2001:db8:5::1 > 2001:db8:5::2: ICMP6, echo reply, id 56760, seq 5, length 64
|
||
10:53:52.926411 IP6 fe80::216:3eff:fe00:2 > 2001:db8:5::2: ICMP6, neighbor solicitation, who has 2001:db8:5::2, length 32
|
||
10:53:52.927121 IP6 2001:db8:5::2 > fe80::216:3eff:fe00:2: ICMP6, neighbor advertisement, tgt is 2001:db8:5::2, length 24
|
||
|
||
|
||
|
||
13:14:32.958532 IP6 2001:db8:5::1 > 2001:db8:5::2: ICMP6, neighbor advertisement, tgt is 2001:db8:5::2, length 32
|
||
0x0000: 0016 3e00 0004 0016 3e00 0602 86dd 6000 ..>.....>.....`.
|
||
0x0010: 0000 0020 3aff 2001 0db8 0005 0000 0000 ....:...........
|
||
0x0020: 0000 0000 0001 2001 0db8 0005 0000 0000 ................
|
||
0x0030: 0000 0000 0002 8800 484c 6000 0000 2001 ........HL`.....
|
||
0x0040: 0db8 0005 0000 0000 0000 0000 0002 0201 ................
|
||
0x0050: 0016 3e00 0602 ..>...
|
||
|
||
```
|
||
13:14:32.958532 IP6 2001:db8:5::1 > 2001:db8:5::2: ICMP6, neighbor advertisement, tgt is 2001:db8:5::2, length 32
|
||
0x0000: 0016 3e00 0004 0016 3e00 0602 86dd 6000 ..>.....>.....`.
|
||
0x0010: 0000 0020 3aff 2001 0db8 0005 0000 0000 ....:...........
|
||
0x0020: 0000 0000 0001 2001 0db8 0005 0000 0000 ................
|
||
0x0030: 0000 0000 0002 8800 484c 6000 0000 2001 ........HL`.....
|
||
0x0040: 0db8 0005 0000 0000 0000 0000 0002 0201 ................
|
||
0x0050: 0016 3e00 0602 ..>...
|
||
```
|
||
|
||
00:16:3e:00:00:02
|
||
|
||
|
||
|
||
这个包是一个 **ICMPv6 邻居通告(Neighbor Advertisement, NA)** 消息,表明发送方(`2001:db8:5::1`)告知接收方(`2001:db8:5::2`),其目标地址(`tgt`)的链路层(MAC)信息。
|
||
|
||
以下是对这个包的逐字段详细分析:
|
||
|
||
------
|
||
|
||
### **1. 数据包的结构**
|
||
|
||
ICMPv6 邻居通告消息由以下几部分组成:
|
||
|
||
| **字段** | **长度** | **解释** |
|
||
| ------------------- | -------- | ------------------------------------------------------ |
|
||
| **以太网帧头** | 14 字节 | 包括源 MAC 地址、目标 MAC 地址和以太网类型。 |
|
||
| **IPv6 头** | 40 字节 | IPv6 源地址、目的地址,及与数据包相关的信息。 |
|
||
| **ICMPv6 头** | 4 字节 | 包括类型(Type)、代码(Code)、校验和(Checksum)。 |
|
||
| **ICMPv6 数据部分** | 可变长度 | 邻居通告消息的具体内容,包括目标地址和链路层地址选项。 |
|
||
|
||
------
|
||
|
||
### **2. 分析具体字段**
|
||
|
||
#### **以太网帧头**
|
||
|
||
```
|
||
0x0000: 0016 3e00 0004 0016 3e00 0602 86dd
|
||
```
|
||
|
||
| 偏移量 | 字段 | 值 | 解释 |
|
||
| -------- | ------------- | ------------------- | --------------------------------------- |
|
||
| `0x0000` | 目标 MAC 地址 | `00:16:3e:00:00:04` | 目标设备的链路层地址(目的 MAC 地址)。 |
|
||
| `0x0006` | 源 MAC 地址 | `00:16:3e:00:06:02` | 源设备的链路层地址(发送方 MAC 地址)。 |
|
||
| `0x000c` | 以太网类型 | `0x86dd` | 表示接下来的数据是 IPv6 数据包。 |
|
||
|
||
------
|
||
|
||
#### **IPv6 头部**
|
||
|
||
```
|
||
0x0010: 6000 0000 0020 3aff 2001 0db8 0005 0000
|
||
0x0020: 0000 0000 0001 2001 0db8 0005 0000 0000
|
||
0x0030: 0000 0000 0002
|
||
```
|
||
|
||
| 偏移量 | 字段 | 值 | 解释 |
|
||
| -------- | ---------------- | --------------- | -------------------------------------------- |
|
||
| `0x0010` | 版本/流量类/流标 | `6000 0000` | IPv6 版本号(6),流量类别(0),流标(0)。 |
|
||
| `0x0014` | 载荷长度 | `0020` | 载荷长度 32 字节。 |
|
||
| `0x0016` | 下一头部类型 | `3a` | 表示下一头部为 ICMPv6(58)。 |
|
||
| `0x0017` | 跳数限制 | `ff` | 初始跳数设置为 255,避免跨链路转发。 |
|
||
| `0x0018` | 源地址 | `2001:db8:5::1` | 发送方 IPv6 地址。 |
|
||
| `0x0028` | 目的地址 | `2001:db8:5::2` | 接收方 IPv6 地址。 |
|
||
|
||
------
|
||
|
||
#### **ICMPv6 头部**
|
||
|
||
```
|
||
0x0030: 8800 484c
|
||
```
|
||
|
||
| 偏移量 | 字段 | 值 | 解释 |
|
||
| -------- | ------------ | ------ | ------------------------------------------------ |
|
||
| `0x0030` | 类型(Type) | `88` | 表示这是一个邻居通告(Neighbor Advertisement)。 |
|
||
| `0x0031` | 代码(Code) | `00` | 固定为 0(邻居通告无子代码)。 |
|
||
| `0x0032` | 校验和 | `484c` | 校验和,确保 ICMPv6 数据的完整性。 |
|
||
|
||
------
|
||
|
||
#### **ICMPv6 数据部分**
|
||
|
||
```
|
||
0x0034: 6000 0000 2001 0db8 0005 0000 0000 0000 0002
|
||
0x0050: 0201 0016 3e00 0602
|
||
```
|
||
|
||
##### **(a) 邻居通告标志和目标地址**
|
||
|
||
```
|
||
0x0034: 6000 0000 2001 0db8 0005 0000 0000 0000 0002
|
||
```
|
||
|
||
| 偏移量 | 字段 | 值 | 解释 |
|
||
| -------- | -------- | --------------- | ---------------------------------- |
|
||
| `0x0034` | 目标地址 | `2001:db8:5::2` | 目标设备的 IPv6 地址,告知请求方。 |
|
||
|
||
##### **(b) 链路层地址选项**
|
||
|
||
```
|
||
0x0050: 0201 0016 3e00 0602
|
||
```
|
||
|
||
| 偏移量 | 字段 | 值 | 解释 |
|
||
| -------- | -------- | ------------------- | ---------------------------------------------------- |
|
||
| `0x0050` | 选项类型 | `02` | 链路层地址选项(Target Link-Layer Address Option)。 |
|
||
| `0x0051` | 选项长度 | `01` | 长度为 1(单位:8 字节)。 |
|
||
| `0x0052` | MAC 地址 | `00:16:3e:00:06:02` | 目标设备的链路层地址(MAC 地址)。 |
|
||
|
||
------
|
||
|
||
### **3. 总结这个包的含义**
|
||
|
||
1. **包类型**:
|
||
- 这是一个 **ICMPv6 邻居通告(NA)** 数据包。
|
||
2. **发送方信息**:
|
||
- IPv6 地址:`2001:db8:5::1`。
|
||
- MAC 地址:`00:16:3e:00:06:02`。
|
||
3. **接收方信息**:
|
||
- 目标 IPv6 地址:`2001:db8:5::2`。
|
||
- 目标链路层地址(MAC):`00:16:3e:00:04`。
|
||
4. **作用**:
|
||
- 通知目标设备(`2001:db8:5::2`),IPv6 地址 `2001:db8:5::1` 解析为 MAC 地址 `00:16:3e:00:06:02`。
|
||
5. **网络流程**:
|
||
- 这是对之前邻居请求(NS)消息的回复,目标设备将更新其邻居表,以便后续通信。
|
||
|
||
------
|
||
|
||
### **补充**
|
||
|
||
- **邻居通告的用途**:
|
||
- 用于响应邻居请求。
|
||
- 通知链路上的其他设备该地址的链路层信息。
|
||
- **校验关键点**:
|
||
- 确认 IPv6 头部和 ICMPv6 数据是否正确匹配。
|
||
- 确保链路层地址和目标地址一致。
|
||
|
||
如果你需要进一步分析或有其他问题,请随时补充!
|
||
=======
|
||
是的,你可以在这个 `tuntap.c` 文件的基础上完成第二问和第三问。以下是如何扩展这个文件来实现处理 ARP 请求和生成 ARP 响应的建议步骤:
|
||
|
||
---
|
||
|
||
### **扩展步骤**
|
||
|
||
#### **1. 增加 ARP 数据包解析和生成的逻辑**
|
||
- 定义 ARP 数据包的结构。
|
||
- 添加解析函数,用于从 `buf` 中提取 ARP 请求包的信息。
|
||
- 添加响应生成函数,用于根据解析结果生成 ARP 响应包。
|
||
|
||
#### **2. 在现有的读取逻辑中嵌入 ARP 处理**
|
||
- 当前的代码已经实现了从 `TUN/TAP` 设备读取数据的功能(`read`)。
|
||
- 在读取的数据中,检查是否为 ARP 请求包(根据协议类型和操作码)。
|
||
- 如果是 ARP 请求,则生成响应数据,并通过设备写回。
|
||
|
||
#### **3. 实现发送 ARP 响应的逻辑**
|
||
- 使用 `write` 系统调用,将生成的 ARP 响应包通过 `tap` 接口发送回去。
|
||
|
||
---
|
||
|
||
### **代码实现(示例)**
|
||
|
||
以下是如何在现有代码基础上扩展实现 ARP 请求解析和响应的代码示例。
|
||
|
||
#### **(1) 定义 ARP 数据包结构和处理函数**
|
||
|
||
在文件顶部增加 ARP 相关的定义和函数:
|
||
```c
|
||
#include <stdint.h>
|
||
#include <string.h>
|
||
|
||
// 定义 ARP 包结构
|
||
typedef struct arp_packet {
|
||
uint16_t hardware_type;
|
||
uint16_t protocol_type;
|
||
uint8_t hardware_len;
|
||
uint8_t protocol_len;
|
||
uint16_t opcode;
|
||
uint8_t sender_mac[6];
|
||
uint8_t sender_ip[4];
|
||
uint8_t target_mac[6];
|
||
uint8_t target_ip[4];
|
||
} arp_packet_t;
|
||
|
||
// 解析 ARP 请求
|
||
int parse_arp_request(const uint8_t *buf, arp_packet_t *arp_req) {
|
||
memcpy(arp_req, buf + 14, sizeof(arp_packet_t)); // 跳过以太网头部
|
||
return ntohs(arp_req->opcode) == 1; // 返回是否为 ARP 请求
|
||
}
|
||
|
||
// 生成 ARP 响应
|
||
void create_arp_response(const arp_packet_t *arp_req, uint8_t *buf) {
|
||
memset(buf, 0, 42); // 清空响应缓冲区
|
||
|
||
// 填充以太网头部
|
||
memcpy(buf, arp_req->sender_mac, 6); // 目标 MAC 地址(原请求的发送方)
|
||
uint8_t mac[6] = {0xDE, 0xAD, 0xBE, 0xEF, 0x00, 0x01}; // 响应方 MAC
|
||
memcpy(buf + 6, mac, 6); // 源 MAC 地址
|
||
buf[12] = 0x08; buf[13] = 0x06; // ARP 协议类型 (0x0806)
|
||
|
||
// 填充 ARP 数据包部分
|
||
arp_packet_t *arp_resp = (arp_packet_t *)(buf + 14);
|
||
arp_resp->hardware_type = htons(1); // 硬件类型 (Ethernet)
|
||
arp_resp->protocol_type = htons(0x0800); // 协议类型 (IPv4)
|
||
arp_resp->hardware_len = 6;
|
||
arp_resp->protocol_len = 4;
|
||
arp_resp->opcode = htons(2); // ARP 响应
|
||
memcpy(arp_resp->sender_mac, mac, 6); // 响应方 MAC
|
||
memcpy(arp_resp->sender_ip, arp_req->target_ip, 4); // 响应方 IP
|
||
memcpy(arp_resp->target_mac, arp_req->sender_mac, 6); // 请求方 MAC
|
||
memcpy(arp_resp->target_ip, arp_req->sender_ip, 4); // 请求方 IP
|
||
}
|
||
```
|
||
|
||
---
|
||
|
||
#### **(2) 修改 `main` 函数,添加 ARP 处理逻辑**
|
||
|
||
在 `main` 函数的 `while` 循环中扩展读取和处理逻辑:
|
||
```c
|
||
uint8_t buf[BUF_LEN];
|
||
uint8_t response_buf[BUF_LEN]; // 用于存储响应数据
|
||
arp_packet_t arp_req;
|
||
|
||
while (running) {
|
||
int nread;
|
||
if ((nread = read(tun_fd, buf, BUF_LEN)) < 0) {
|
||
perror("ERR: Read from tun_fd");
|
||
break;
|
||
}
|
||
|
||
printf("Read %d bytes from device %s\n", nread, dev);
|
||
|
||
// 检查是否为 ARP 包
|
||
if (nread >= 42 && buf[12] == 0x08 && buf[13] == 0x06) {
|
||
printf("ARP packet detected\n");
|
||
|
||
// 解析 ARP 请求
|
||
if (parse_arp_request(buf, &arp_req)) {
|
||
printf("Processing ARP request from %d.%d.%d.%d\n",
|
||
arp_req.sender_ip[0], arp_req.sender_ip[1],
|
||
arp_req.sender_ip[2], arp_req.sender_ip[3]);
|
||
|
||
// 生成 ARP 响应
|
||
create_arp_response(&arp_req, response_buf);
|
||
|
||
// 发送 ARP 响应
|
||
if (write(tun_fd, response_buf, 42) < 0) {
|
||
perror("ERR: Write to tun_fd");
|
||
} else {
|
||
printf("Sent ARP response\n");
|
||
}
|
||
}
|
||
}
|
||
}
|
||
```
|
||
|
||
---
|
||
|
||
### **功能验证**
|
||
1. **启动 `tuntap.c` 程序**:
|
||
```bash
|
||
sudo ./tuntap mytap0
|
||
```
|
||
|
||
2. **使用 `arping` 测试**:
|
||
在另一台主机上运行以下命令:
|
||
```bash
|
||
arping -I mytap0 <tap0 对应的 IP 地址>
|
||
```
|
||
程序应打印检测到 ARP 请求,并生成和发送 ARP 响应。
|
||
|
||
---
|
||
|
||
### **总结**
|
||
- 第二问通过定义 `arp_packet_t` 数据结构和解析/生成函数,设计了一个合适的接口。
|
||
- 第三问通过扩展 `tuntap.c` 文件,增加了 ARP 请求处理和响应功能。
|
||
- 使用 `arping` 工具可以测试实现的正确性。
|